Introduction
The rise of EtherHiding, a malicious software campaign, has introduced a novel approach to distributing malware via the Binance Smart Chain. This article sheds light on the sinister tactics employed by cybercriminals and how they manipulate blockchain technology to their advantage.
EtherHiding Operation
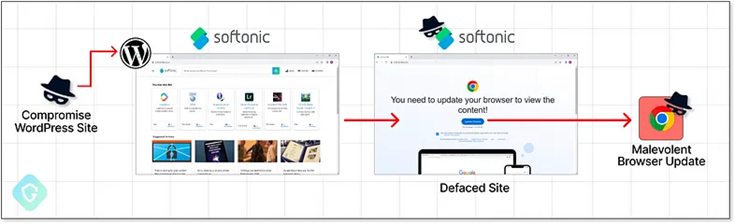
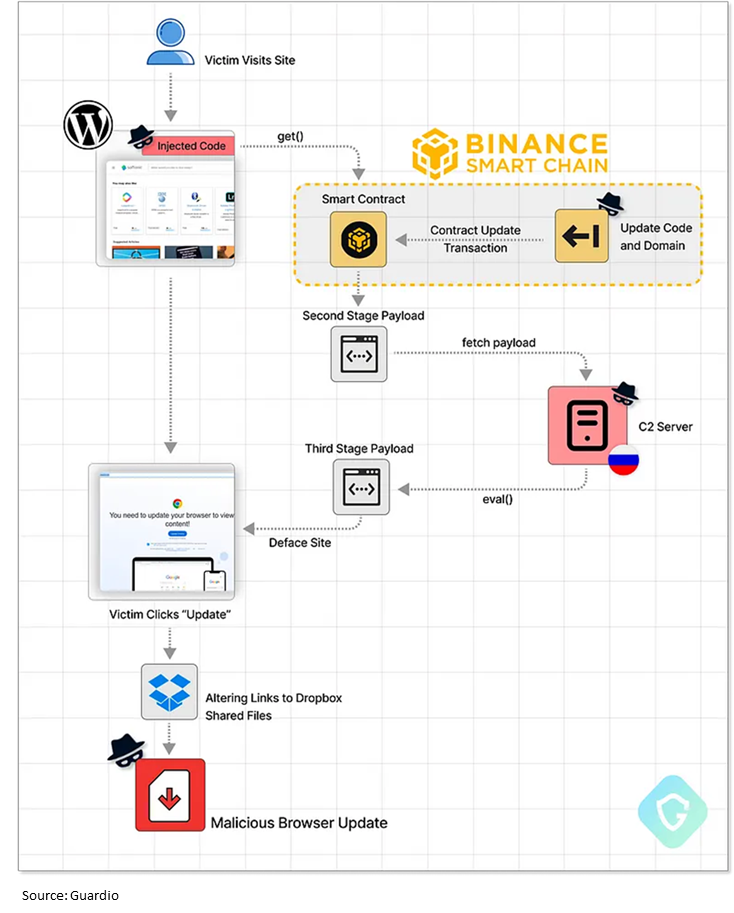
Security researchers have shared a breakdown of the technique at Guardio Labs. EtherHiding’s operation spanned over two months and initially exploited compromised WordPress sites to deceive users into downloading fake “browser updates.” When the attackers’ initial hiding place, Cloudflare Worker hosts, was dismantled, they turned to the blockchain, making detection and takedown more challenging. They deface websites, forcing users to update their browsers, leading to malicious infostealer malware downloads, plunging users into digital threats.
The Initial Assault
The campaign starts on compromised WordPress sites, embedding a nefarious JavaScript code within article pages. This code serves as the “bridgehead” and fetches a second-stage payload from the attackers’ server, enabling website defacement. As Cloudflare stopped hosting, the attackers ingeniously turned to blockchain technology for “Bullet Proof” hosting.
Script Tags: The Silent Invader
Malicious actors use script tags to compromise WordPress sites by exploiting vulnerable plugins, outdated software, or stolen credentials. The code interacts with the Binance Smart Chain, creating a blockchain contract controlled by the attackers. Binance Smart Chain, akin to Ethereum, offers decentralized app and smart contract support.
Mitigating the Menace
Blockchain’s decentralized nature makes it challenging to combat EtherHiding. The primary defense is community and developer vigilance. WordPress site owners must maintain robust security measures, update plugins, secure credentials, and monitor on-site activities. Traditional methods of blocking domains and IPs fall short against blockchain-based threats.
Summary
EtherHiding is a new and complex malware threat that uses blockchain technology to distribute malicious code. Protecting against it requires a combination of vigilance and updated security practices. As cybercriminals continue to evolve, the battle against such threats remains ongoing.




