In today’s digital landscape, where we are more connected than ever before, the need for robust cybersecurity measures has never been greater. Imagine your computer or network as a fort and the firewall as the protective shield that guards its gates. This is precisely what a firewall does in the world of cybersecurity – it acts as a barrier between your trusted internal network and the potentially dangerous world of the internet.
In this article, we’ll delve into the fundamental aspects of firewalls, explaining their importance, how they work, and why they are your essential shield against a wide range of cyber threats.
Understanding Firewalls
What Is a Firewall?
A firewall is a network security device or software that monitors and filters incoming and outgoing network traffic based on an organization’s previously established security policies. Simply, it acts as a gatekeeper, allowing or blocking data traffic depending on predefined rules.
Why Are Firewalls Important?
Firewalls are crucial for several reasons:
- Protection: They protect your network from unauthorized access, cyberattacks, and malicious software.
- Privacy: They safeguard your sensitive data from being compromised or stolen.
- Compliance: In many industries, using firewalls is a regulatory requirement to ensure data security.
Types of Firewalls
There are various types of firewalls, each with its own approach to filtering network traffic. Let’s explore the most common ones:
1. Packet Filtering Firewalls
Packet filtering firewalls examine packets of data as they arrive at a network’s entrance. They allow or block packets based on predefined criteria, such as source and destination IP addresses, ports, and protocols.
These firewalls are efficient and work at high speeds. They’re suitable for basic security needs.

2. Stateful Inspection Firewalls
Stateful inspection firewalls examine individual packets and track the state of active connections. They make decisions based on the context of the traffic, not just individual packets.
They provide more advanced security by considering the state of the connection. They can detect and block various forms of attacks, including session hijacking.
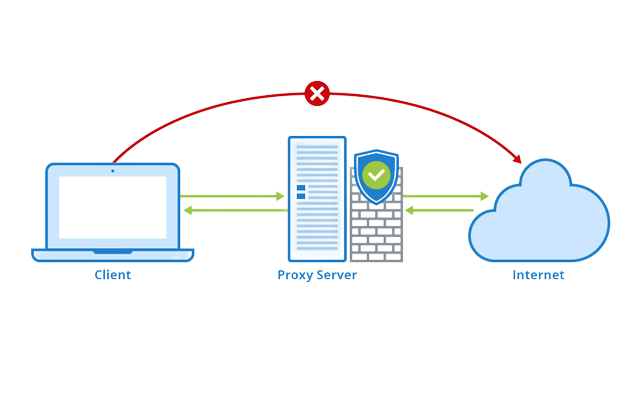
3. Proxy Firewalls
Proxy firewalls act as intermediaries between the user’s device and the internet. They receive requests from users and forward them on behalf of the user. The response from the internet is also routed through the proxy before reaching the user.
They add an extra layer of security by hiding the user’s IP address and providing content filtering capabilities.
4. Application Layer Firewalls (Next-Generation Firewalls)
These firewalls operate at the application layer of the OSI model, which means they can inspect and filter traffic at the application level. They are more advanced and can identify specific applications or services.
They provide granular control over applications and can detect and block sophisticated threats.
How Firewalls Protect You?
Blocking Unauthorized Access: Firewalls ensure that only authorized users and devices can access your network or specific services. They do this by inspecting incoming traffic and comparing it against the predefined rules.
Filtering Malicious Traffic: Firewalls can identify and block traffic that matches known attack patterns or signatures, such as viruses, malware, and intrusion attempts.
Content Filtering: Some firewalls have content filtering capabilities that allow you to control and monitor the type of content accessed from your network. This is particularly useful for businesses and organizations.
Logging and Reporting: Firewalls can generate logs and reports, helping you track network activity, identify security incidents, and comply with regulatory requirements.
What Are the Best Practices for Firewall Security?
To make the most of your firewall’s protective capabilities, consider these best practices:
- Regular Updates: Keep your firewall’s firmware and software up to date to ensure it can effectively identify and block new threats.
- Customized Rules: Tailor firewall rules to match your organization’s specific security requirements.
- Monitoring and Alerts: Set up monitoring and alert systems to be promptly informed of any unusual or suspicious network activity.
- Regular Audits: Conduct periodic audits of your firewall’s rules and configurations to ensure they align with your organization’s security policies.
- Education: Train your staff on safe internet practices to minimize the risk of inadvertently allowing malicious traffic through the firewall.
Conclusion
Firewalls are the unsung cybersecurity heroes, silently standing guard to protect your network and data from constant cyber threats. Understanding their importance and implementing best practices can significantly enhance your organization’s security posture. In a world where cyber threats are ever-evolving, a strong and well-maintained firewall remains your steadfast shield against the unknown dangers of the digital era.




