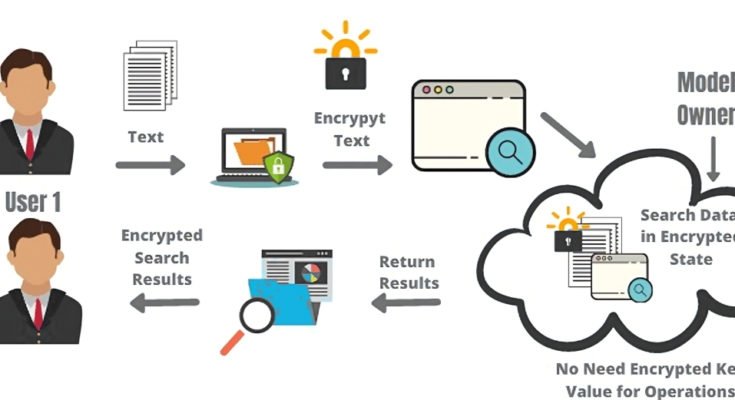
In our data-driven era, the demand for secure computation is crucial. Balancing privacy and functionality poses a challenge for traditional encryption methods. Enter homomorphic encryption – a revolutionary solution allowing computations on encrypted data without compromising security.
Homomorphic encryption resolves the dilemma of safeguarding data while retaining its usability. Unlike traditional methods, it enables direct computations on encrypted data, ushering in a new era of secure data processing. This article explores the principles and applications of homomorphic encryption, offering insights for cybersecurity enthusiasts, tech professionals, and anyone curious about the evolving landscape of data security.
Let’s dive deep and study how the power of homomorphic encryption can be harnessed.
What is Homomorphic Encryption?
Homomorphic encryption represents a groundbreaking advancement in cryptography, allowing computations to be performed on encrypted data without the need for decryption. At its core, homomorphic encryption relies on mathematical algorithms that enable operations on ciphertext, maintaining the confidentiality of the original data throughout the computational process. This innovative approach ensures that sensitive information remains secure, even when subjected to various mathematical operations.
Types of Homomorphic Encryption
Partial Homomorphic Encryption
Partial homomorphic encryption allows for evaluating a specific mathematical operation on encrypted data. While it supports addition or multiplication operations, it falls short of providing the capability to perform both operations simultaneously. Despite this limitation, partial homomorphic encryption remains a practical choice for certain applications where specific computations are the primary focus.
Somewhat Homomorphic Encryption
Somewhat homomorphic encryption takes a step further by permitting the evaluation of a limited number of both addition and multiplication operations on encrypted data. While it does not offer the complete functionality of fully homomorphic encryption, somewhat homomorphic schemes balance versatility and computational efficiency. This makes them suitable for various privacy-preserving applications, including secure data processing in cloud environments.
Fully Homomorphic Encryption
The pinnacle of homomorphic encryption (FHE), fully homomorphic encryption enables executing an arbitrary number of addition and multiplication operations on encrypted data. FHE allows for complete computational flexibility, making it a powerful tool for privacy-preserving applications that require complex computations while maintaining the utmost security. Although FHE comes with increased computational overhead, ongoing research and advancements aim to enhance its efficiency for broader practical adoption.
How Homomorphic Encryption Works?
A. Encryption Process
The homomorphic encryption process initiates the conversion of plaintext data into ciphertext while preserving its confidentiality. Unlike traditional encryption methods, homomorphic encryption ensures that computations can be conducted directly on the encrypted data. Encryption involves intricate mathematical operations, creating a ciphertext that conceals the original information’s meaning. This ciphertext can then be safely transmitted or processed without decryption.
B. Secure Computation
Homomorphic encryption’s distinctive feature is its ability to perform secure computations on encrypted data. While traditional encryption methods require decryption before any computation, homomorphic encryption enables operations such as addition and multiplication to be executed directly on the ciphertext. This allows parties to perform computations on sensitive data without exposing unencrypted information. Secure computation ensures that the results derived from these encrypted operations are meaningful and accurate, providing a transformative approach to privacy-preserving data processing.
C. Decryption without Compromising Privacy
The decryption phase in homomorphic encryption is equally critical. When the computation is complete, the encrypted result is decrypted to reveal the outcome in plaintext. Importantly, this decryption occurs without compromising the privacy of the original data. The decrypted result is only visible to authorized parties, ensuring that sensitive information remains confidential throughout the entire process. This unique capability distinguishes homomorphic encryption from conventional methods, offering a secure and privacy-preserving solution for various applications, including cloud computing and data analysis.
Advantages of Homomorphic Encryption
Homomorphic encryption offers a range of advantages that make it a compelling solution for privacy-preserving data processing.
- Privacy Preservation: Homomorphic encryption allows computations on encrypted data without decryption, ensuring the privacy of sensitive information throughout the process.
- Secure Outsourcing: Organizations can securely outsource data processing tasks to third-party providers, maintaining the confidentiality of their data even when computations are performed externally.
- Data Utilization: The ability to perform meaningful computations on encrypted data enables data analysis and utilization without compromising privacy, opening new possibilities for secure analytics.
- Compliance with Regulations: Homomorphic encryption aligns with data protection regulations by providing a robust solution for secure data processing, supporting compliance efforts across various industries.
Homomorphic Encryption Challenges
While homomorphic encryption brings significant advantages, it is not without its challenges. Performing operations on encrypted data incurs computational overhead, making homomorphic encryption more resource-intensive than traditional encryption methods.
The additional computational requirements may result in increased latency and response times, impacting the performance of systems employing homomorphic encryption.
Integrating homomorphic encryption into existing systems can be complex, requiring careful consideration of application-specific requirements and potential trade-offs.
Ongoing Research and Innovations in Hybrid Encryption
Researchers and practitioners are actively addressing the challenges associated with homomorphic encryption. Ongoing research focuses on optimizing homomorphic encryption algorithms to reduce computational overhead and enhance overall efficiency.
Hybrid encryption approaches combining homomorphic encryption with other cryptographic techniques are being explored to balance security and performance.
Initiatives are underway to standardize homomorphic encryption, facilitating broader adoption and interoperability across different platforms and applications.
Conclusion
Homomorphic encryption emerges as a pivotal player in secure data processing, offering a revolutionary approach to preserving privacy without sacrificing functionality. Its unique ability to enable computations on encrypted data ensures that sensitive information remains confidential throughout various operations. Homomorphic encryption is not just a protective shield for data; it is an enabler of secure computation, allowing organizations to harness the power of their information while safeguarding it from unauthorized access. Its role extends beyond conventional encryption methods, providing a robust solution for scenarios where privacy is paramount.
In the digital era, where data is a currency and privacy is paramount, homomorphic encryption emerges as a beacon of security, shaping the landscape of secure computation for years.