In today’s interconnected world, cybersecurity is a topic that affects us all. We’ve all heard about hackers and cybercriminals using complex technical tactics to breach security systems, but another equally potent threat often flies under the radar – social engineering. Social engineering is a form of cyberattack that relies on manipulating human psychology rather than exploiting technical vulnerabilities. It’s like a digital scam game; anyone can fall victim to it.
In this article, we’ll explore the world of social engineering, its various forms, and most importantly, how you can recognize and resist these deceptive tactics. Whether you’re a tech enthusiast or simply someone who uses the internet, the insights shared here will empower you to protect your personal and business information from these crafty cybercriminals.
Understanding Social Engineering
Before we delve into defending against social engineering, it’s crucial to understand what it is. At its core, social engineering is the art of manipulating people into revealing confidential information or performing actions that compromise security. This can take many forms, and attackers often exploit our emotions, trust, and willingness to help.
Types of Social Engineering Attacks
Phishing
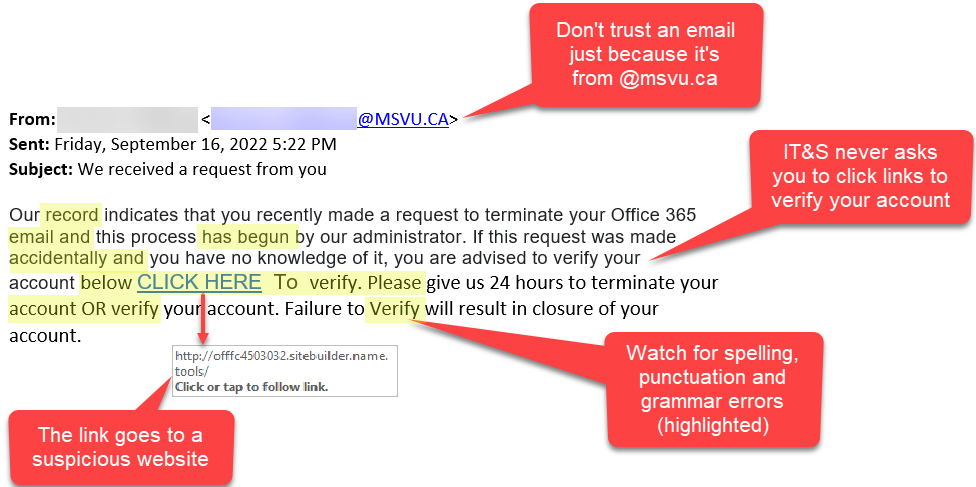
Phishing emails or messages are designed to trick you into revealing sensitive information like passwords or credit card numbers. They often impersonate trusted organizations, urging you to click on malicious links or download harmful attachments.
Pretexting
Attackers create a fabricated scenario or pretext to manipulate you into divulging information. This could involve impersonating a colleague, claiming an urgent need for information, and using persuasive storytelling.
Baiting
Cybercriminals offer enticing files or downloads, often luring victims with free software or media. Once you download the bait, malware is unleashed on your device, compromising your security.
Tailgating
In physical social engineering, an attacker gains unauthorized access to a secure location by following an authorized person closely, relying on their trust to gain entry.
Why Social Engineering Matters
Social engineering attacks are not just theoretical threats; they are real and can have devastating consequences. Falling victim to a social engineering attack can lead to identity theft, financial losses, and damage to your reputation. It can also be a gateway for more extensive cyberattacks affecting individuals and organizations.
Recognizing Social Engineering Attacks
The first line of defense against social engineering is awareness. By recognizing the signs of these attacks, you can take steps to protect yourself. Here are some key indicators to watch out for:
Unsolicited Communication
Be cautious when you receive unsolicited emails, messages, or phone calls asking for sensitive information. Verify the identity of the sender or caller before sharing any data.
Urgency and Pressure
Social engineers often create a sense of urgency, pressuring you to act quickly without thinking. Take a moment to evaluate the situation and verify the request.
Requests for Personal Information
Legitimate organizations typically don’t ask for sensitive information like passwords or Social Security numbers through email or messages. Be skeptical of such requests.
Suspicious Links and Attachments
Hover over links to reveal the actual URL before clicking. Avoid downloading files from unknown sources or emails with unexpected attachments.
Verify Identities
When in doubt, verify the identity of the person or organization making the request. Use official contact information, not the information provided in the suspicious communication.
Trust Your Gut
It probably is if something feels off or too good to be true. Trust your instincts and blunder on the side of caution.
Resisting Social Engineering Attacks
Now that you know how to recognize social engineering attempts, let’s explore strategies to resist them effectively:
Educate Yourself and Others
Stay informed about the latest social engineering tactics and share this knowledge with employees. Awareness is a powerful defense.
Use Strong Passwords and Multi-Factor Authentication
Create strong, unique passwords for each account, and enable multi-factor authentication whenever possible. This adds an extra layer of protection.
Verify Requests
If someone requests sensitive information or actions that seem suspicious, verify their identity through a trusted channel. Don’t rely solely on the initial communication.
Be Cautious on Social Media
Limit the personal information you share on social media platforms. Cybercriminals often use this information to tailor their attacks.
Keep Software and Systems Updated
Regularly update your operating system and software to patch known vulnerabilities. Cybercriminals often target outdated systems.
Employ Security Software
Install reputable antivirus and anti-malware software on your devices. It can help detect and prevent malicious activities.
Conclusion
In a world where technology plays an integral role in our daily lives, defending against social engineering is a responsibility we all share. By recognizing the signs of social engineering attacks and implementing effective defense strategies, we can protect ourselves and our digital identities from falling prey to cybercriminals.
Cybercriminals are constantly evolving their tactics, so staying vigilant and informed is the key to staying safe in the digital age. Share this knowledge with your colleagues and employees.




